Cryptographic Engineering & Side-Channel Analysis Lab
Our research covers, but is not limited to, the following topics
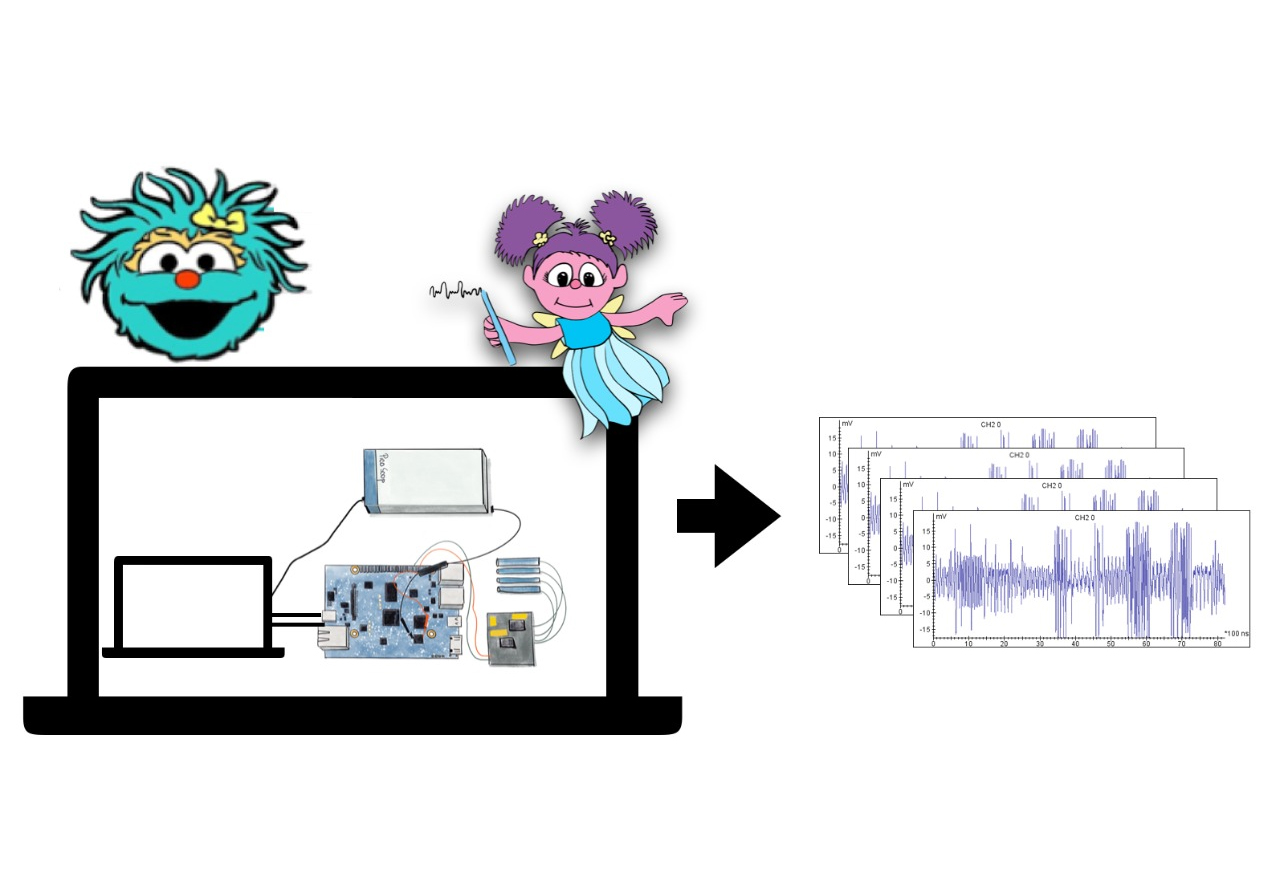
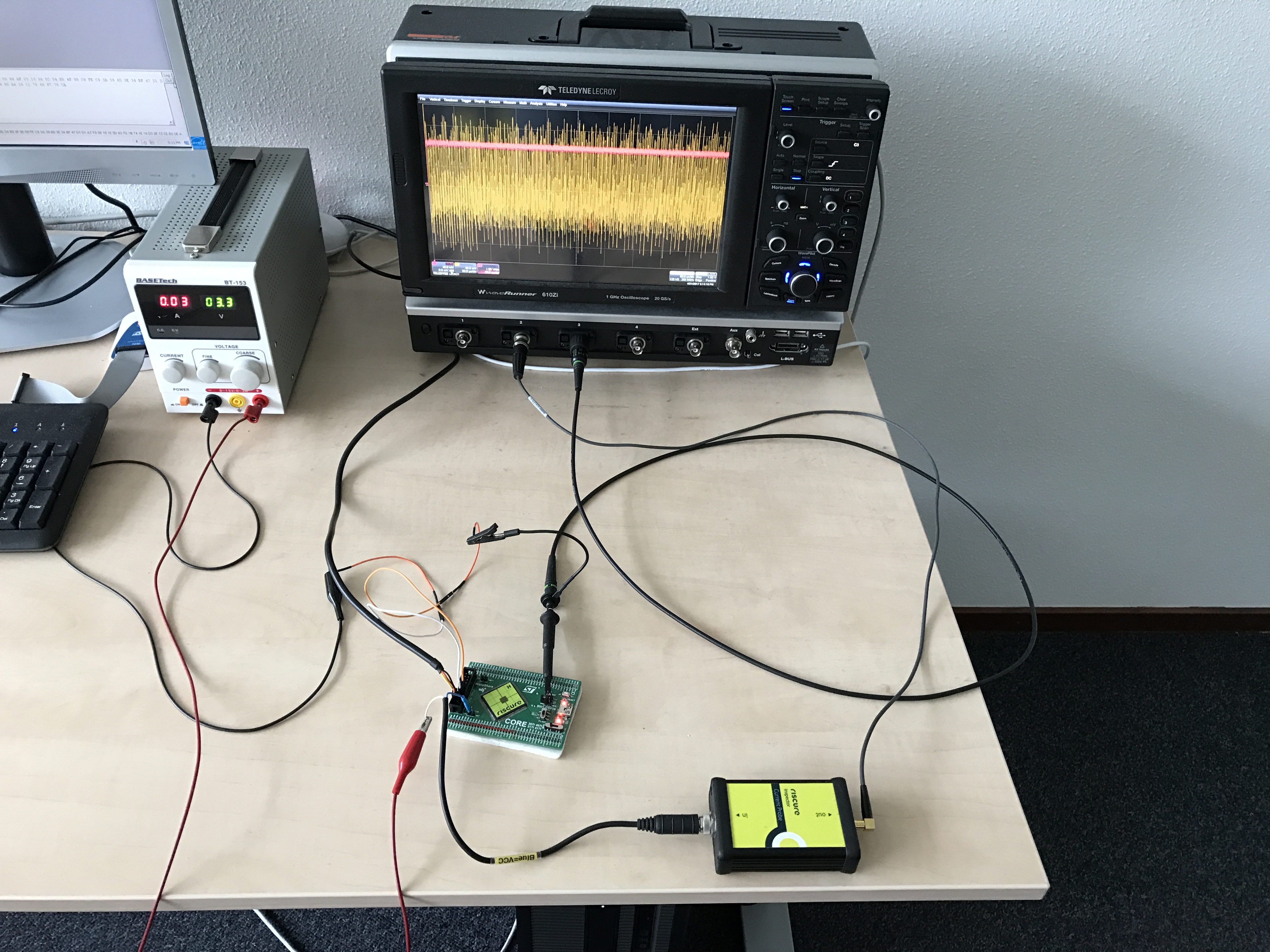
Physical attacks on embedded crypto devices
We evaluate the security of smartcards, mobile phones and IoT devices by exploiting power and EM measurements and fault injection. The goal is to come up with mitigations against those attacks.
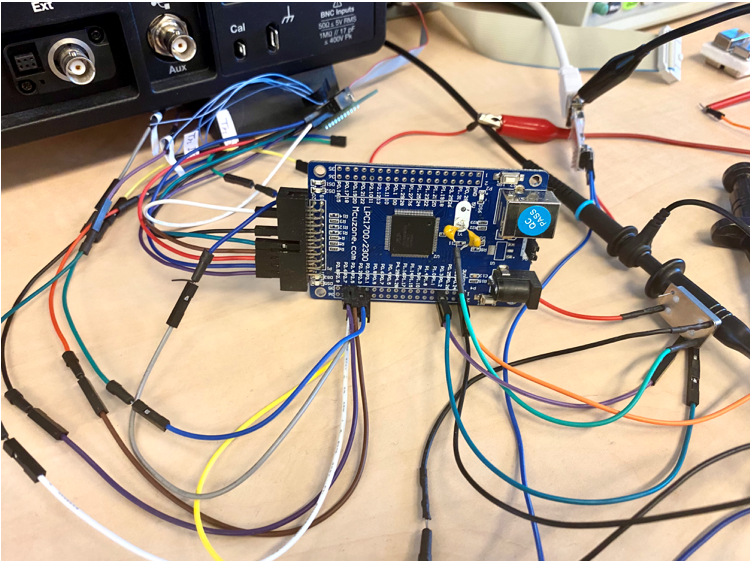
Secure cryptographic implementations
Crypto implementation should resist attacks that are of concern in real-world use cases. Such hardened implementations should fit the constraints on performance, power and energy.
FPGA security
FPGAs are increasingly popular platforms thanks to their (software-like) ability to be reconfigured after deployment and their (hardware-like) high performance and low power consumption. In securing FPGA-based systems, reconfigurability is an asset that can be used for protection against physical attacks.

AI and security
AI methods have become common in security evaluations of embedded devices. Conversely, implementations of neural nets are often considered trade secrets. Attack vectors to reverse engineer neural nets is using side channels and fault injection. We are working on both of those research directions, so AI for security and the security of AI.
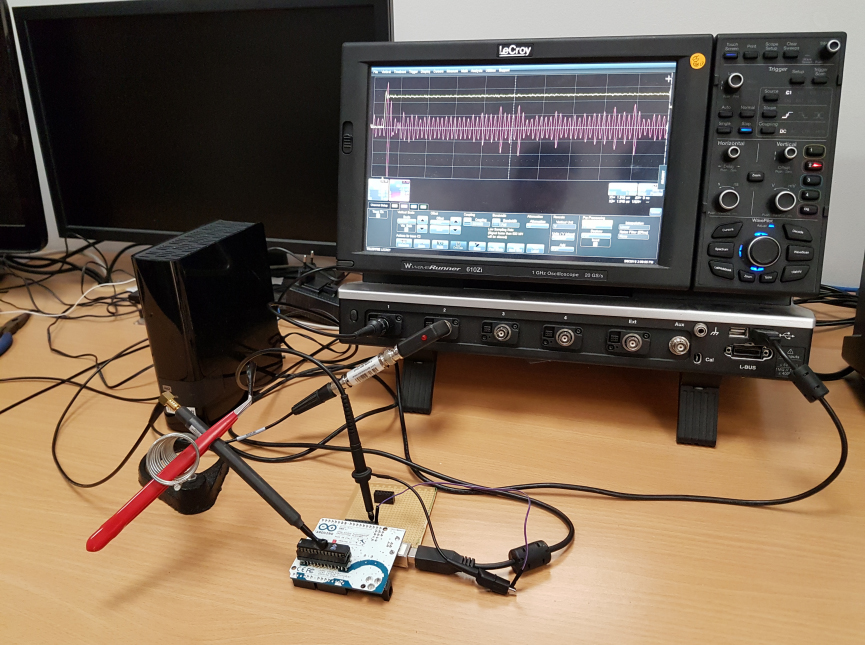
Lightweight cryptography
Lightweight crypto is important to ensure security in constrained environments. We work on efficient implementations of such algorithms in hardware and software considering relevant physical attacks.
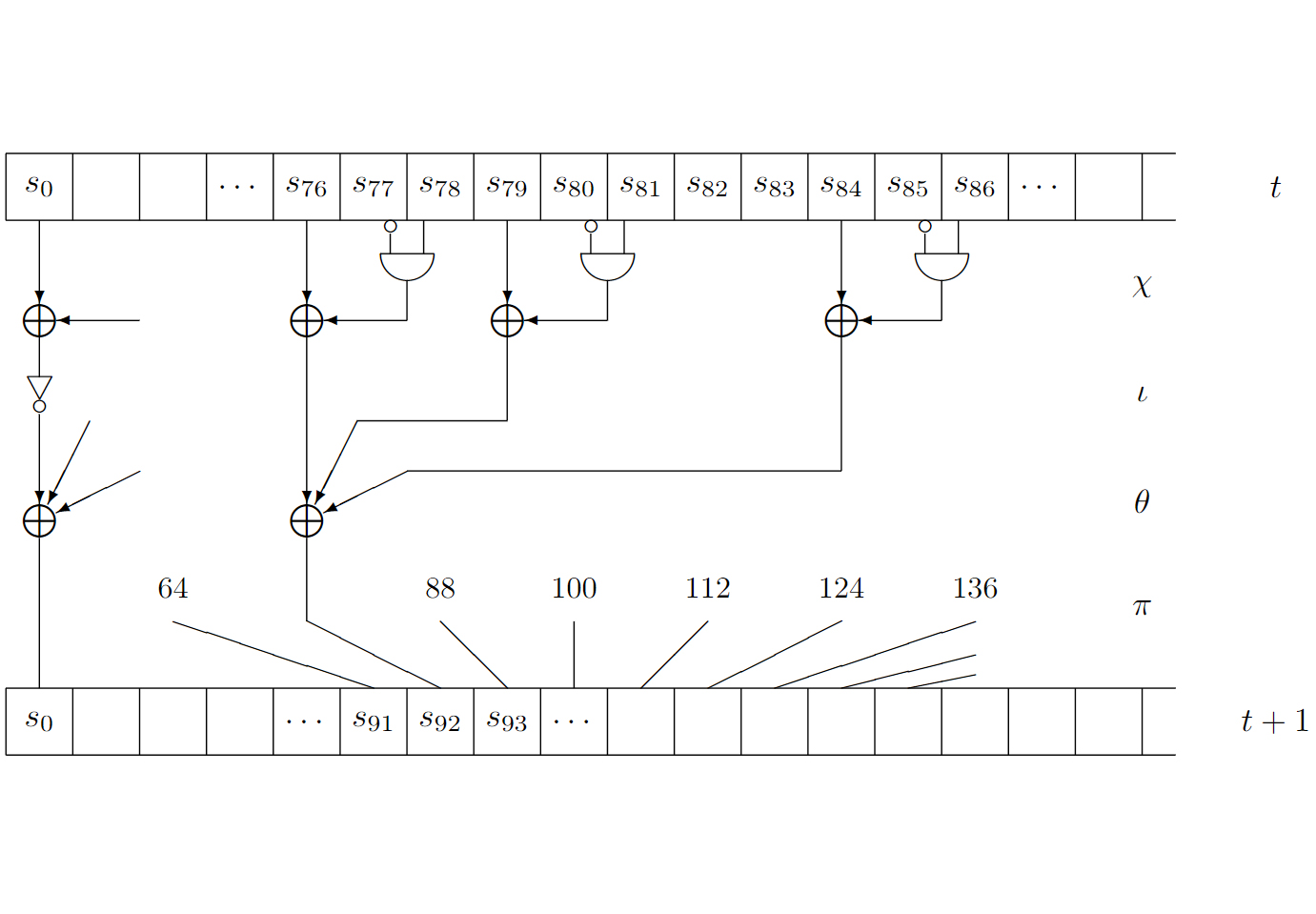
Leakage simulators
A leakage simulator allows the transformation of high-level code into traces similar to those collected from the target architecture. We work on the next generation of tools to automate the creation of secure hardware.